Many folks have heard of a “VPN” (Virtual Private Network), but if you’re not in the IT profession, or you haven’t taken the time to do your research, do you really understand what they are and what they do? When we do hear about VPNs on the internet, the radio, or TV, we hear about how VPNs will “Secure” our internet traffic and keep our communications “Private” from prying eyes. Is that really true and do you really need one to be safe on the internet? Let’s talk about it:
For most folks out there, our digital lives consist mainly of surfing the web, perusing Facebook, Instagram, TikTok, or other social media sites, checking email, paying bills, checking your bank account, sending and receiving Venmos or PayPal, and perhaps other activities. When we are doing these things, we are literally putting our lives, personal information, financial information, and even our safety and security out on the internet with the hope that the other parties with which we share that information will use that data for good purposes. I’m not here to discuss whether those entities are doing that, what we are here to discuss is whether the path to reach those entities is actually secure or private. In doing that, let’s first discuss how basic internet traffic works:
The “Internet” is a series of switches and routers and many millions-of-miles of cable that connect them to each other. That’s it. Literally. When we want to visit some server in California, and we are physically in New York, we must traverse that network of routers and switches hop by hop until we reach the other server. Your data may pass through 15-20 routers en route to it’s destination. In doing so, every inch of wire, every router, and every switch that your data passes through can see that you are passing data from your location to the server’s location at the other end. Curious to see an actual example? If you are on a Mac or linux, open your terminal and type in:
traceroute yahoo.com
If you’re using Windows, type in:
tracert yahoo.com
Make sure you type the commands exactly as seen (copy and paste is even better). What you are doing is seeing every single router between you and Yahoo at the time you issue the command.
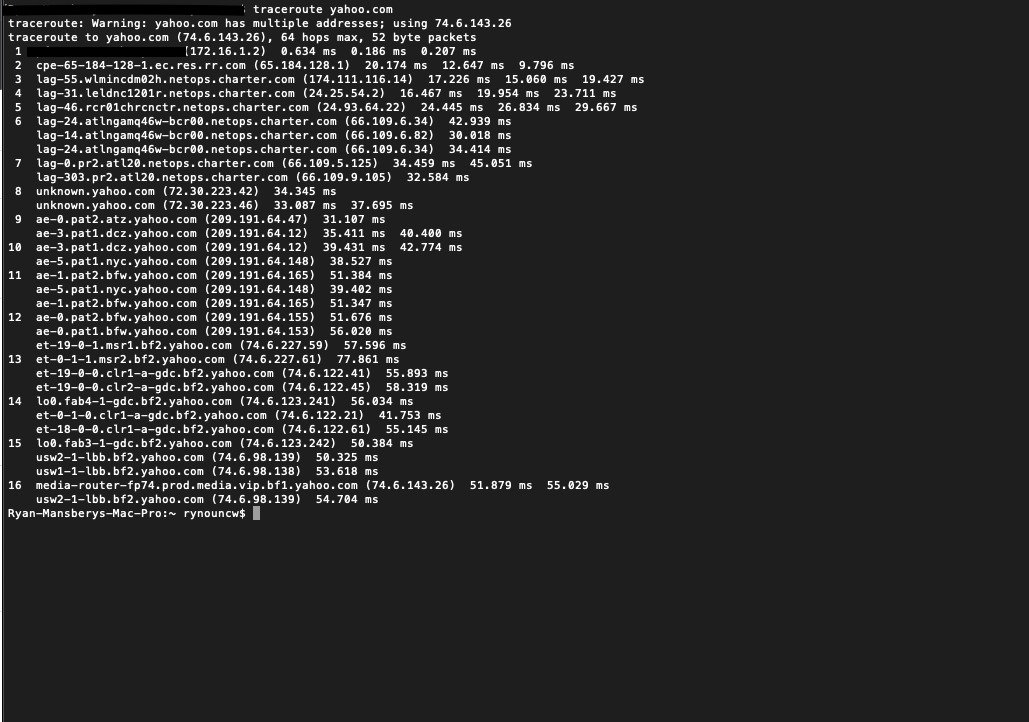
Ignore the lines that have 2, 3, or more IP addresses per line…..those are just showing that there are multiple routes (paths the information can take) available at that hop. This is called redundancy and it is what keeps the internet running when routers fail. Based on this, we can deduce that between my house and yahoo.com, my traffic will pass through no less than 16 routers. Each time my request goes into a router, its packet, which is both the data I’m sending plus all the information needed to tell the routers how to get it there, is read to try and figure out where it must be sent to reach its intended destination. By reading the packet, if the packet is to be sent to another router, it passes the packet verbatim with the exception of a few small addressing changes which aren’t necessarily relevant to this discussion. The big takeaway from this is that every packet you sent is capable of being read (or actually is read) by each router it passes through. This should scare you. What if you put your social security number in to check on your tax refund? 15 routers on the internet or so all saw it. Don’t freak out yet, because if the destination server is using encryption, your social security number won’t be in easily readable form, it will be encrypted and look like a bunch of random characters. We will get into this more below.
So, let’s say we decide we are going to “Go” to Yahoo to read a news story. By that, I mean get on your internet browser and type in yahoo.com, open the yahoo app, or otherwise get to Yahoo. Assuming we don’t have the numerical IP address of yahoo.com in at our system’s disposal already (think of the IP address as literally the address or GPS coordinates of the destination server), we must look up the IP address of the other party. Computers are very good at doing exactly what you tell them, and they are also not capable of doing anything that you don’t explicitly ask them to do. They don’t know what to do with “yahoo.com,” they only understand IP addresses, so we need to go out and get the IP address of our destination for our computer to know what to do with it. There are servers out there called “DNS” servers which do exactly that: Take yahoo.com and turn it into a IP address that your computer/device can understand. So, we reach out to the DNS server that is in charge of serving us to get the numerical IP address for yahoo. To do that, we will also have to traverse through the routers of the internet to get the DNS server.
So back through the internet we go to get to the DNS server. The DNS request packet we send is sometimes encrypted, sometimes it’s not (this will depend on your particular DNS server). If it’s not encrypted, it will be in plain readable form as is passes through each router. Why is this important? Well, each router you pass through now sees that you were looking for the IP address of that site, even before you actually visit the site. Most of the time, it’s no big deal. Millions of people every day visit yahoo.com to read news articles, so why would I care if my Internet Service Provider and other downstream Internet Service Providers whose routers you pass through knows I went to Yahoo?
It’s a matter of privacy. Just like we don’t want people watching what we do at home, at work, in our cars, and anywhere else in our daily lives (even if it is happening), we don’t want anyone snooping on what we do on the internet. The only problem with that is that your internet service provider owns part of the path between you and Yahoo, so you have to use their equipment to get there. As such, they can see that request, and they use the fact that you went to yahoo.com to read a news article and sell that information to third parties who can tailor ads, or other services to you. It’s really staggering how good they’ve gotten at this. Have you ever had a conversation with a friend or family member about wanting to look at some product out there, and as soon as you open your phone the next time, there are ads for that product popping up? That’s not an accident, it’s precisely what I mention above. It also means that government entities that follow the proper channels can get information about what you do on the internet relatively easy. Here is what a regular, run-of-the-mill DNS lookup looks like to those who might intercept your traffic:
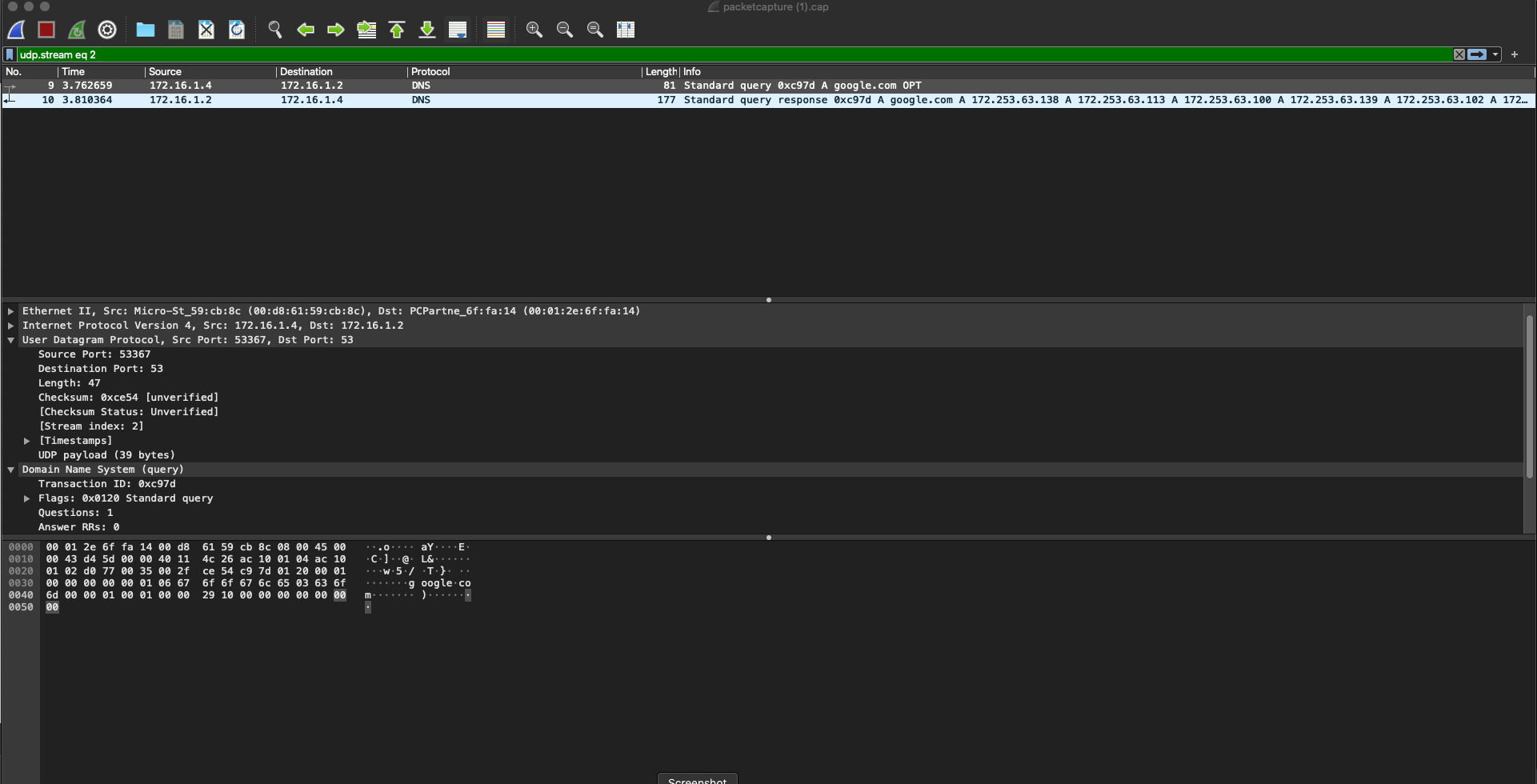
We use a program called Wireshark, which is freely available and extremely powerful, to view the actual contents of packets flowing over a network. If you look at the “Protocol” column, it clearly says “DNS.” If you look in the bottom box, you can even see some form of the word “Google” in there (I did a DNS lookup of Google for this example). So, with little fanfare, anyone at your ISP now knows that you looked up how to get to Google. Fairly innocuous to most, but what if you were looking up something a little more taboo?
Now that you’re at least aware of what’s going on with your internet traffic, and possibly now scared of what can happen, how do we protect ourselves from it? One option that you’ve probably heard of is called a “VPN.” It stands for Virtual Private Network, and can help shield (but not completely prevent) your traffic from being viewed by your ISP or the government.
Think of it this way: Lets say you want to mail a letter to someone across the country, but you don’t want anyone to know what you’re sending, or even want anyone to know that you sent anything. How would you accomplish this? You can use a “Security envelope,” which has a bunch of extra protection on the inside of the envelope so that nobody can read what’s in the envelope without opening it. The only problem is…your address is still in the return address part and the recipient’s address is still on the envelope. You have to use either the USPS, or UPS or FedEx (or others) to send the letter, so someone will know that you sent a letter once it reaches their distribution system. Enter the “Virtual Proxy eNvelope” service.
I know…it’s a cheesy, not exact play on “VPN”, but bear with me. Let’s say there was a service out there that attempted to anonymize your outgoing and incoming mail. Here’s how what might look: In a “Wrapper” (think a box, or bigger envelope), you put the mail you want to send. On the outside of the wrapper, you address it to the VPN service, and put your return address on it. When it gets to the VPN service, they open the box, take the envelope out, and on the outside of the envelope, the VPN puts their return address on it. There is a code added to the return address so that it can be later identified, something the the VPN service knows, but nobody else is supposed to know. When your recipient mails a response back, they address it to the VPN (including the code), and the recipient puts his or her address on the return address portion. When the VPN gets the package, they box it back up, send it to you, with the VPN’s return address on it, and the cycle is complete. Now the delivery services only know that the VPN sent a letter to your recipient, and you sent a package to the VPN, but since the VPN keeps their activities secret, your actual packages can’t be tied back to you.
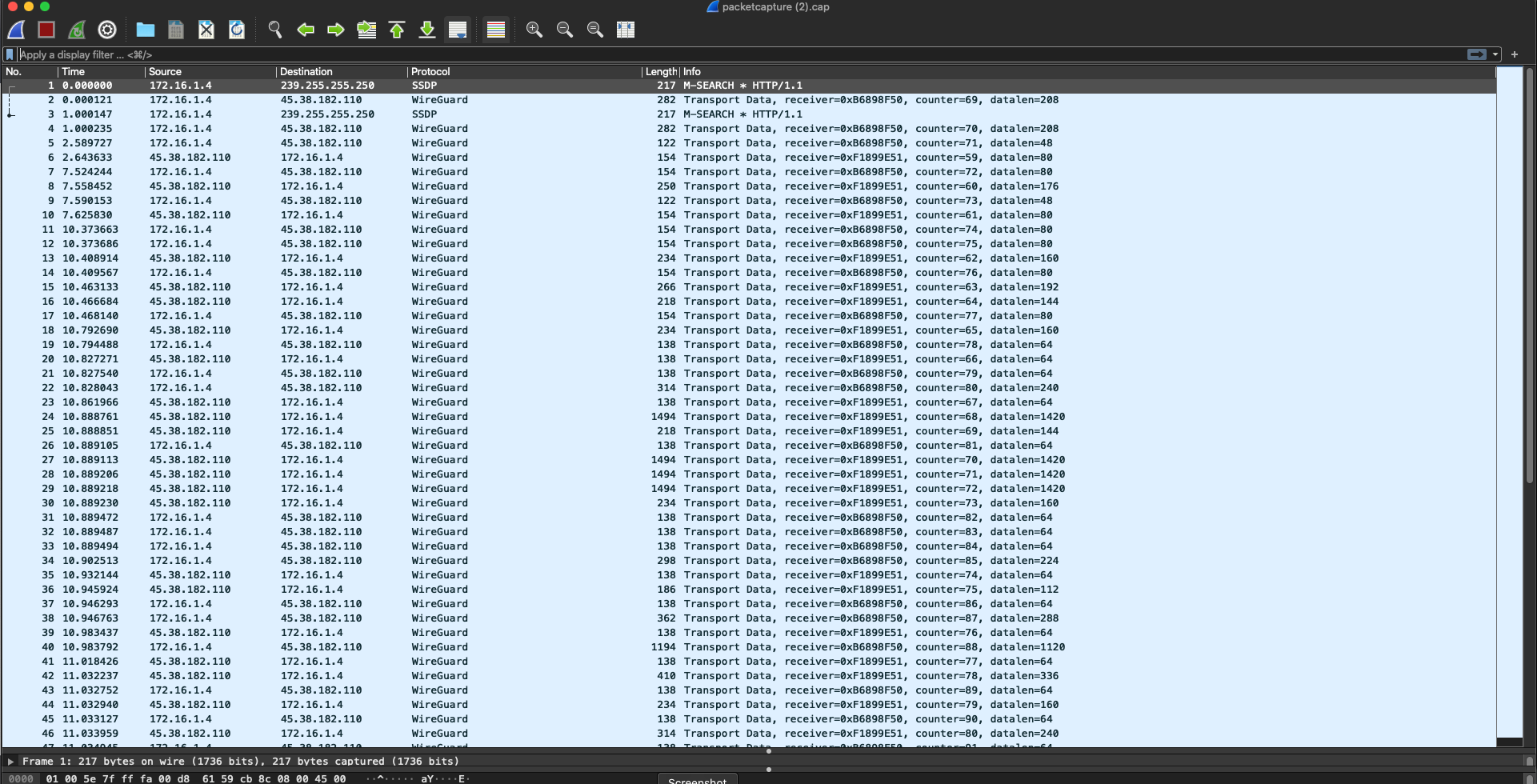
Now let’s look at the same DNS traffic after connecting to a VPN provider. I am using NordVPN in this case, but regardless of which provider you use, your traffic will look something like this:
What you will notice is that now all of our traffic is labeled as “WireGuard” (which is the VPN protocol NordVPN and I are using to communicate), and it all looks the same. This is like the “wrapper” I mention above. You can’t tell what is a DNS query, what is website traffic, it all looks the same. Not only does it look the same, it is also encrypted, so if we look at it in depth, it’s going to look like scrambled text.
Before we go any further, let’s talk about encryption, because it’s important to this discussion at this point. If you visit a website, and it has the indication of security in the address bar (this will differ on different browsers), the information you exchange with that server is encrypted. What that means is that you send text that is not in a readable format unless you have the encryption keys to decrypt the information. When you first make contact with that website, you and the server do what’s called a key exchange to make sure you each have a unique set of encryption keys for that conversation so that no outsiders can decrypt the data without stealing the keys from you and the server. That means that those routers in the internet we talked about above can see the destination IP address(ie….they can see that you are sending data to the server at yahoo.com), but can’t read what you’re sending the server (and vice versa).
Here’s the other kicker. Nobody cares that you went to Yahoo’s website to read some lame news story…..but what if you had your curiosity get the best of you, and you go search for a nude picture of Kim Kardashian? Or with all of the political unrest going on, let’s say you went to the NRA’s website but didn’t want the government to know about it? Or worse….. You’d probably want to hide that traffic from as many folks as possible, right?
This where a VPN might help you.
In the above examples, when we use the DNS servers to look up an IP address, those requests have certain fingerprints that say “I am a DNS request,” even if they are encrypted. Most unencrypted DNS requests go out over port 53, and are UDP traffic, so to someone looking at that traffic passing through, if they see a packet that is UDP and headed for port 53, that’s almost certainly a DNS request.
Let’s say we want to do a DNS lookup while connected to a VPN. All traffic, regardless of what it is, where it is going, or its intended purpose travels through what’s called a “tunnel,” or an encrypted channel. All traffic flows on 1 port, and to anyone who might capture these packets in between your computer and the VPN server, all of these packets look almost exactly the same no matter what. So, you can’t tell what packets are DNS requests, website requests, or anything else, they are all just encrypted data intended for the VPN server. When your request reaches the VPN server, it is decrypted, and sent out from the VPN server’s IP address. The response is sent back to the VPN server, which then encrypts it again and sends it back down the tunnel to you. You will sacrifice some speed for the added privacy.
Here is where you need to be the most careful if you select a VPN: Most VPN providers have what’s called “No Log Policies,” meaning that they do not keep logs on what traffic you are creating. If the VPN provider logs your traffic, it can be subpoenaed in court, or sold to 3rd parties to generate income for the VPN. Some of these VPN companies that supposedly have no log policies have been subpoenaed and produced logs, so take what they say with a grain of salt, and be very picky in selecting one if you do decide to use one.
What can we take away from this?
VPNs can help you protect yourself from ISPs and potentially the government looking at your internet activities, so long as the VPN service has a “no logs” policy (which means that they don’t log your activity), and actually adhere to that practice. Otherwise, your activity might be traceable, even if it is harder.